Mandatory Algorithms for Coding Interview
Basic algorithms that you must know if you want to crack your coding interview. In case you are starting to prepare for coding practice then make sure you...

When I started learning Cloud being a webdev and software architect background. I came across many IT lingo, jargons, abbreviations that I did know about them. In this post, I am writing all those in one place. I hope this will help you as well on your cloud Azure/AWS/GCP Solution Architect journey!
Remote Authentication Dial-In User Service (RADIUS) is a networking protocol that provides centralized authentication, authorization, and accounting management for users who connect and use a network service. RADIUS was developed by Livingston Enterprises in 1991 as an access server authentication and accounting protocol.
Extensible Authentication Access Protocol over LAN
Media Access Control Address: It uniquely identifies the device in the network. 48-bit hexadecimal number that is hard-coded on a NIC.
Return on Investment
independent software vendor
SAN: storage area network (SAN) By default, Azure VMs are assigned drive D to use as temporary storage
Application Request Routing (ARR) is a feature where when a client (or browser) request to any Azure based website, a cookie will be created and stick to the first time request received web site instance.
A virtual machine running in Azure can now be associated with a direct and publicly accessible IP address that sticks to the VM for its lifetime.
A network security group (NSG) contains a list of security rules that allow or deny network traffic to resources connected to Azure Virtual Networks (VNet). NSGs can be associated to subnets or individual network interfaces (NIC) attached to VMs.
A Network Interface (NIC) enables an Azure Virtual Machine to communicate with internet, Azure, and on-premises resources. When creating a virtual machine using the Azure portal, the portal creates one network interface with default settings for you.
Role-based access control (RBAC) is a policy-neutral access-control mechanism defined around roles and privileges. The components of RBAC such as role-permissions, user-role and role-role relationships make it simple to perform user assignments.
Configuration Management Database
A Rack has servers (Virtual Machines) in a data-center.
Stock Keeping Unit (SKU) Learn more about SKU types in Azure
(formerly FhGFS) is a parallel file system, developed and optimized for high-performance computing.

Portable Batch System (or simply PBS) is the name of computer software that performs job scheduling.
Apache Spark is a fast and general engine for large-scale data processing. It has a Scala, Java, and Python API and can be run either on either a single node or multi-node configuration. For both cases, it is recommended to have exclusive access of the node in Slurm.
Simple Linux Utility for Resource Management (SLURM) is a free and open-source job scheduler for Linux and Unix-like kernels, used by many of the world’s supercomputers and computer clusters.
In order to run an application using a spark context it is first necessary to run a Slurm job which starts a master and some workers.
Virtual Private Network (VPN). In Azure VPN is a type of Virtual Network Gateway.
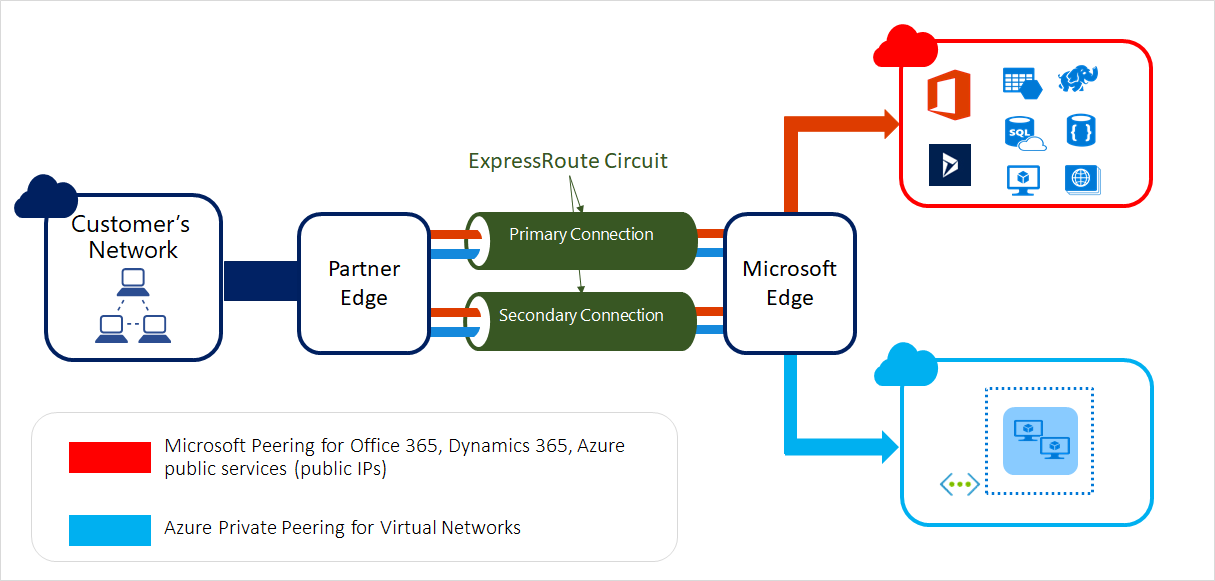
ExpressRoute (ER) lets you extend your on-premises network into the Microsoft cloud over a private connection with the help of connectivity provider.
A demilitarized zone (DMZ) is a perimeter network that protects an organization’s internal local-area network (LAN) from untrusted traffic.
Virtual IP address aka front-end. VIP is an IP address that doesn’t correspond to an actual physical network interface.
A dynamic IP (DIP) pool is a range of IP addresses.
“Border Gateway Protocol (BGP)” is a standardized exterior gateway protocol designed to exchange routing and reachability information between autonomous systems (AS) on the Internet.

Local Site Network (LSN)
Internet Key Exchange
The Local Network Gateway (LNG) typically refers to your on-premises location. Learn…
Classless Inter-Domain Routing (CIDR). It is an IP address assigning method that improves the efficiency of address distribution. It is also known as supernetting that replaces the older system based on classes A, B, and C networks. By using a single CIDR IP address many unique IP addresses can be designated.
The Apache HTTP Server, colloquially called Apache (ə-PATCH-ee) is a free and open-source cross-platform web server software, released under the terms of Apache License 2.0. Apache is developed and maintained by an open community of developers under the auspices of the Apache Software Foundation.
Apache Hadoop is a collection of open-source software utilities that facilitates using a network of many computers to solve problems involving massive amounts of data and computation. It provides a software framework for distributed storage and processing of big data using the MapReduce programming model.
All the modules in Hadoop are designed with a fundamental assumption that hardware failures are common occurrences and should be automatically handled by the framework.
A small Hadoop cluster includes a single master and multiple worker nodes. The master node consists of a Job Tracker. A slave or worker node acts as both a DataNode and Task Tracker. All machines are connected by SSH.

Hadoop distributed file system (HDFS) The Hadoop distributed file system (HDFS) is a distributed, scalable, and portable file system written in Java for the Hadoop framework. Hadoop splits files into large blocks and distributes them across nodes in a cluster.
Checks the file system and file system metadata of a volume for logical and physical errors. If used without parameters, chkdsk displays only the status of the volume and does not fix any errors. If used with the /f, /r, /x, or /b parameters, it fixes errors on the volume.
Open Command prompt in windows and run chkdsk

If you want to run chkdsk on D drive and fix issues then run chkdsk d: /f
Network File System (NFS)
New Technology File System or simply NTFS is a proprietary journaling file system developed by Microsoft in 1993. Starting with Windows NT 3.1, it is the default file system of the Windows NT family.
Hierarchical File System (HFS) developed by Apple for MAC OS in 1998. One file size up to 2GB only.
Extended File System (EXT). The extended file system, or ext, was implemented in April 1992 as the first file system created specifically for the Linux kernel.
Virtual Machine File System (VMFS)
Server Message Block (SMB)

Secure File Transfer Protocol
Fully Qualified Domain Name (FQDN)
Azure Database Migration Service
NoSQL databases (aka “not only SQL”) are non tabular, and store data differently than relational tables. NoSQL databases come in a variety of types based on their data model. The main types are document, key-value, wide-column, and graph. They provide flexible schemas and scale easily with large amounts of data and high user loads.
Apache Cassandra is a free and open-source, distributed, wide-column store, NoSQL database management system designed to handle large amounts of data across many commodity servers, providing high availability with no single point of failure.
Gremlin is a graph traversal language and virtual machine developed by Apache TinkerPop of the Apache Software Foundation. Gremlin works for both OLTP-based graph databases as well as OLAP-based graph processors.
Cloud Service Provider (CSP)
Cloud Service Offering (CSO)
Certificate Signing Request
Defense Information Systems Agency (DISA) is a U.S combat support agency that connects the U.S military and government though IT and communications support. Originally known as the defense communications industry (DCA), the agency was created in 1960, partially in response to communication issues during WWII.
Cloud Computing Security Requirement Guide
The Federal Risk and Authorization Management Program (FedRAMP) provides a standardized approach to security authorizations for Cloud Service Offerings. The Federal Risk and Authorization Management Program (FedRAMP) was established in 2011 to provide a cost-effective, risk-based approach for the adoption and use of cloud services by the federal government. FedRAMP empowers agencies to use modern cloud technologies, with an emphasis on security and protection of federal information.
https://www.fedramp.gov/program-basics/
FedRAMP+ is the concept of leveraging the work done as part of the FedRAMP assessment, and adding specific security controls and requirements necessary to meet and assure DoD’s critical mission requirements. A CSP’s CSO can be assessed in accordance with the criteria outlined in this SRG, with the results used as the basis for awarding a DoD provisional authorization.
The Department of Defense (DoD) is responsible for providing the military forces needed to deter war and protect the security of our country. The major elements of these forces are the Army, Navy, Marine Corps, and Air Force, consisting of about 1.3 million men and women on active duty.
The National Institute of Standards and Technology (NIST) is a non-regulatory government agency that develops technology, metrics, and standards to drive innovation and economic competitiveness at U.S.-based organizations in the science and technology industry.
Integrated Windows Authentication (IWA)
Certificate Authority (CA) like Entrust, Thwate, Verisign
Domain Name System (DNS) is the phonebook of the Internet.
User Defined Routing (UDR)
Network Address Translation (NAT)
Secure Shell (SSH) protocol used to communicate machines. It encrypts the data while sending data to other machine. It works on applciation layer (layer-7) of OSI model.
Teletype Network (Telnet) developed in 1969. Plain text communication between machines. Good for LAN since data in not encrypted. Not good for sensitive data. It works on applciation layer (layer-7) of OSI model.
Source Network Address Translation (SNAT) allows traffic from a private network to go out to the internet. Virtual machines launched on a private network can get to the internet by going through a gateway capable of performing SNAT. The device performing NAT changes the private IP address of the source host to public IP address.

Destination Network Address Translation (DNAT) : Destination NAT changes the destination address in the IP header of a packet.
Network Virtual Appliances (NVAs): An NVA(Network Virtual Appliance) is typically used to control the flow of network traffic from a perimeter network, also known as a DMZ, to other networks or subnets.
Internal Load Balancer(ILB) is a security enhancement over the current public load balancing that is offered in Azure.
High Available Ports: High availability (HA) ports is a type of load balancing rule that provides an easy way to load-balance all flows that arrive on all ports of an internal Standard Load Balancer.
Network Attached Storage (NAS)
Redundant Array of Inexpensive/independent Disks(RAID). It was created in 1988 as a means to combat the rising cost of disk drives. You’ll often hear RAID as it relates to network attached storage or “NAS”. You know in movies when you see the “mainframe” and it’s rows and rows of hard drives backing up all of the evil corporation’s information? That’s NAS, and that’s RAID in action. RAID Wikipedia
Annual Loss Expectancy
ALE = SLE x ARO
Single Loss Expectancy
Annualized Rate of Occurrence
CIA - Confidentiality, Integrity and Availability. The CIA Triad is actually a security model that has been developed to help people think about various parts of IT security.
Intrusion Prevention System
Intrusion Detection System
web application firewall (WAF)
Lightweight Directory Access Protocol “Address Book” of user accounts used to authenticate users. Identifies level of acess, group membership etc.
Structured Query Language(SQL)
fully qualified domain names (FQDNs)
Destination Network Address Translation (DNAT)
Wireless Access Point (WAP)
Internet Control Message Protocol (ICMP) is one of the protocols of the TCP/IP suite. The ICMP echo request and the ICMP echo reply messages are commonly known as ping messages.
Distributed denial of service (DDoS) Learn More. In a distributed denial-of-service (DDoS) attack, an attacker attempts to overwhelm a targeted server or network with junk network traffic — somewhat like bombarding a restaurant with fake delivery orders until it cannot provide service to legitimate customers.
A workgroup is a collection of computers that each maintain their own security information. Here the security is distributed, not centralized.
A domain is a collection of computers where security is handled centrally.Each domain has one or more domain controllers.
Internet Control Message Protocol (ICMP) is a control protocol, meaning that it designed to not carry application data, but rather information about the status of the network itself. The best known example of ICMP in practice is the ping utility, that uses ICMP to probe remote hosts for responsiveness and overall round-trip time of the probe messages.
Universal Resource Locator (URL)
Open System Interconnection (OSI)
🏆 Pro Tip
Top Down: All People Seems To Need Data Processing.
Bottom Up: Please Do Not Through Sausage Pizza Away.
In networking, a protocol is a specified way of formatting data so that any networked computer can interpret the data.
Protocols and their ports:
User Datagram Protocol (UDP) is a connection-less transportation protocol. UDP is used to pass the actual user data. Communication is datagram oriented, so the integrity is guaranteed only on the single datagram. Datagrams reach destination and can arrive out of order or don’t arrive at all. It’s generally used for real time communication, where a little percentage of packet loss rate is preferable to the overhead of a TCP connection. It is an Transport layer (layer-4) protocol. UDP, the User Datagram Protocol, does not set up these dedicated connections.
Transmission Control Protocol (TCP) TCP is a connection oriented transportation protocol. TCP is used to pass the actual user data. It guarantees that all sent packets will reach the destination in the correct order. TCP, the Transmission Control Protocol, sets up dedicated connections between devices and ensures that all packets arrive.
Secure Sockets Layer (SSL) now it is deprecated. It is session layer protocol. It is presentation and session layer protocol. It lies between Transport and application layer.

Transport Layer Security (TLS) provides communications security over a computer network. It is presentation and session layer protocol. It lies between Transport and application layer.

Internet Protocol (IP)
Internet Protocol Security (IPSec): IPsec is a group of protocols that are used together to set up encrypted connections between devices. IPsec is often used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come from. IPsec uses UDP because this allows IPsec packets to get through firewalls.
IPsec is not one protocol, but a suite of protocols. Internet Protocol (IP) is not part of the IPsec suite, IPsec runs directly on top of IP. The following protocols make up the IPsec suite:
Authentication Header (AH): The AH protocol ensures that data packets are from a trusted source and that the data has not been tampered with, like a tamper-proof seal on a consumer product. These headers do not provide any encryption; they do not help conceal the data from attackers.
Encapsulating Security Protocol (ESP): ESP encrypts the IP header and the payload for each packet — unless transport mode is used, in which case it only encrypts the payload. ESP adds its own header and a trailer to each data packet.
Security Association (SA): SA refers to a number of protocols used for negotiating encryption keys and algorithms. One of the most common SA protocols is Internet Key Exchange (IKE).
Reference: https://www.cloudflare.com/learning/network-layer/what-is-ipsec/
All data sent over a network is broken up into smaller pieces called packets, and all packets have two parts: the payload and the header. The payload is the packet’s actual contents, the data being sent. The header has information about where the packet comes from and what group of packets it belongs to. Each network protocol attaches a header to each packet.
Encapsulating packets within other packets is called “tunneling”.
To understand why this is called “tunneling,” we can change the analogy slightly. If a car needs to pass from Point A on one side of a mountain to Point B on the other side, the most efficient way is to simply go through the mountain. However, ordinary cars are not capable of going straight through solid rock. As a result, the car has to drive all the way around the mountain to get from Point A to Point B.
But imagine that a tunnel was created through the mountain. Now, the car can drive straight from Point A to Point B, which is much faster, and which it could not do without the tunnel.
Generic Routing Encapsulation, or GRE, is a protocol for encapsulating data packets that use one routing protocol inside the packets of another protocol. “Encapsulating” means wrapping one data packet within another data packet, like putting a box inside another box. To understand how this works, think about the difference between a car and a ferry. A car travels over roads on land, while a ferry travels over water. A car cannot normally travel on water — however, a car can be loaded onto a ferry in order to do so.
Reference: https://www.cloudflare.com/learning/network-layer/what-is-gre-tunneling/
Internet Protocol Version (IPV). IPv6 is more advanced and has better features compared to IPv4.
Network Time Protocol (NTP) is a networking protocol for clock synchronization between computer systems over packet-switched, variable-latency data networks.
The Tabular Data Stream (TDS) Protocol is an application-level protocol used for the transfer of requests and responses between clients and database server systems. a TDS session is established when the transport-level connection is established and the server receives a request to establish a TDS connection. It persists until the transport-level connection is terminated (for example, when a TCP socket is closed).

Online Transactional Processing (OLTP)
Online Analytical Processing (OLTP)
Simple Mail Transfer Protocol (SMTP) to send emails.
Data Definition Language (DDL)
Korea-Information Security Management System (K-ISMS)
Business-To-Consumer (B2C)
Independent Software Vendor (ISV) - also known as a software publisher, is an organization specializing in making and selling software, as opposed to computer hardware, designed for mass or niche markets.
line-of-business (LOB) - used only for your company or your employees.
IT Service Management (ITSM) Few ITSM tools are ServiceNow, System Center Service Manager, Provance, Cherwell. You can use IT Service Management Connector in Azure to connect your own ITSM tools.
Security Incident and Event Monitoring (SIEM) - Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution.
Virtual Network: This is Private network on Azure Cloud.
Virtual Private Cloud (VPC) this is similar to VNet in Azure.
Elastic Compute Cloud (EC2) Instance: This is a Virtual Machine on Amazon.
user principal name (UPN)
security principal name (SPN)
Microsoft Authentication Library (MSAL)
Active Directory Authentication Library (ADAL)
Active Directory Authentication Library (ADAL) integrates with the Azure AD for developers (v1.0) endpoint, where MSAL integrates with the Microsoft identity platform. Learn More…
OpenID Connect (OIDC) - authentication and authorization protocol
Managed Identity Resource Provider (MSRP)
Azure Advanced Threat Protection ( ATP ) - Now it is known as “Microsoft Defender for Identity”
Self-Service Password Reset
Security Support Provider Interface (SSPI) is a component of Windows API that performs a security-related operations such as authentication.
Dynamic Host Configuration Protocol (DHCP) : related to IP Addressing.
DHCP helps ensure that devices ultimately correctly configured to join networks. DHCP does this by assigning IP addresses and other information to each host (or device) connecting to a network.
Delta query enables applications to discover newly created, updated, or deleted entities without performing a full read of the target resource with every request.
DevOps teams because they can combine metrics and queries.Jupyter Notebook.| FrontDoor | Traffic Manager |
|---|---|
| Http and Https protocol | Used for File and Image |
| Used for multi region app, agnostic of PIP public IP | Used for sharing and accessing multi-region deployed Files and Images, agnostic of PIP public IP |
500 VNets, You can only have one VPN Gateway with 1 VNet.
Basic algorithms that you must know if you want to crack your coding interview. In case you are starting to prepare for coding practice then make sure you...
Application and Service Principal Objects in Azure
Did you get a phone call from your customer saying they want to improve their application reliability while you move their workload to the cloud? If yes t...
Creating cost optimized highly scalable cloud architecture is challenging but it is possible! Using Spot Amazon Elastic Compute Cloud (Amazon EC2) instanc...
In a traditional data center you create one perimeter, secure them by installing firewall, WAF, SIEMS etc. and have 100% confidence that the data center i...
How to make sure our workload in the cloud is secure, reliable. How to monitor the cost of your cloud resources consumption? Is there any automation you can ...
EBITDA and EBIT is a very fundamental financial term that is nowadays mostly considered during the cloud adoption phase for IT companies. If your company ...
Are you attempting coding interview challenges in Javascript? Then make sure you learn below mandatory JavaScriipt apis and utilities.
Point of presence is a fundamental block of the telecommunication domain. You must be aware of this concept. If you want to system design for video conten...
Are you planning to design your next advanced distributed architecture? Make sure you are aware of the concepts such as high availability, consistency and...
Now a days distributed architecture is common. We deploy our services into many different servers to scale them up and meet our demand. However, managing ...
Do you have situations where a process is trying to use your virtual machine in the cloud and you want to protect and control the access? Do you want to u...
Azure Active Directory (AD) verifies the credentials that are username and password. It belongs to the Azure Identity Platform.
Learn more about how to use tags to organize your Azure resources and management hierarchy. Also learn the cmdlet used to fetch tags from Azure resources.
If you have any project that you want to integrate with Azure Active Directory and secure your app. Then you must try using Microsoft Authentication Libra...
Learn the failover and failback stages in Site Recovery on Azure. Learn Business Continuity and Disaster Recovery (BCDR) strategy in Azure.
Site Recovery is very critical now a days. In your own Data-center or Server disasters can happen and you must secure your site to recover from them. Use ...
Securing your workload and datacenter over the cloud is very challenging. You want your resources to be protected by both machines and users. Azure Active...
Data is very essential and now a days data is everything. So you have application in cloud and want to explore which type of data where to store in Azure....
Are you planning to migrate your on-premise data to the cloud using Azure data transfer solutions?
Learn what service from Azure you should use while creating your application in Azure. This article has quick short answer for when to use what in Azure s...
Virtualization is the single concept that now-a-days cloud service providers are using at massive scale and delivering IT technologies such as storage, co...
According to Statista.com As of 2021, around 50 percent of all corporate data is stored in the cloud. This share reached 30 percent in 2015 and has contin...
Azure Network Watcher is a monitoring service with lots of other important services for network. Most network diagnostics issues can be detected and analy...
Why do you care about encryption strategies? Well if you are planning to become system administrator or solution architect then you must know how you woul...
Do you have a lot of JavaScript projects using GitHub repositories? How are you managing dependencies among those projects? Developers might be struggling...
Are you willing to become cloud solution architect? I am going to add a few important technical questions that you must know for your next cloud solution ...
Did you know By default azure storage accounts are accessible by the public internet. How can u restrict all public traffic in to your azure storage accou...
If you want to become Cloud Security Architect you must have basics of Networking. This article will discuss all fundamental concepts of networking. Learn...
What are Azure Monitor and Application Insights? How exactly Azure Monitor work? How can you visualize Application Map with Application Insights? Learn th...
When you want to move your business to cloud the major thing to consider is storage. What kind of data you can store? What is the pricing? How can you opt...
Learn about malware, attacks to the network, social engineering attacks from scratch.
Learn how many types of monitoring services available in Azure to monitor your applications.
Azure Monitor is the central service that can help you to improve performance of your application and dependencies. In this article I will go through the ...
When I started learning Cloud being a webdev and software architect background. I came across many IT lingo, jargons, abbreviations that I did know about ...
When I started learning Azure being a webdev and software architect background. I came across many IT lingo, jargons, abbrebiations that I did know about ...
Blob Storage is helpful to upload images, videos, documents, pdfs etc. over the Azure cloud. In order to create new Azure Blob Storage. You must need to c...
Azure architects must aware of fundamentals of routing and peering. In this article we will see fundamentals as well as we will see some examples of routi...
Azure Storage account is a resource in Azure. Storage Account will give your group of services like Blob Service, File Service, Table Service, Queue Servi...
What are the two reasons that you may see the message: “There are no offers available in your region or country at this time”?
Azure VNet is the fundamental unit of networking in Azure Cloud. You must know the basics of VNet. In this article we will explore Azure VNet.
What is NAT, SNAT, DNAT etc. Why do we need them? What is the role of firewall in a Network and how firewall works with NAT, DNAT? Are you also seeking an...
What is NAT, SNAT, DNAT etc. Why do we need them? What is the role of firewall in a Network and how firewall works with NAT, DNAT? Are you also seeking an...
LRS (locally redundant storage) ZRS (zone redundant storage) GRS (geographically redundant storage) RA GRS (read-access geographically redundant storage) GZR...
A virtual private network (VPN) is a type of private interconnected network. VPNs use an encrypted tunnel within another network. I will explain what is V...
Azure Storage has no upfront cost, no termination fees and pay only for what you use. In this article you will learn about Azure storage access tiers and ...
Are you wondering how can you separately track the billing of your resources allocated in same subscription? Did you think you could save money by turning...
Azure Core Storage Services
How to manage DEV, QA and PROD environments in Azure Cloud? You end-up creating many resources and now how would you organize them for QA, DEV, UAT enviro...
Did you know you can containerize your asp.net MVC with docker application and upload to Azure Container Registry and host them using Azure Kubernetes Clu...
Understanding Core Azure Services
TCP: is a transport-layer protocol, and HTTP is an application-layer protocol that runs over TCP.
Azure portal is great while visualizing Azure log and metrics. You can see the pie chart, graph for resources like VMs etc. You can also create your custo...
In this article you will learn how you can upload a file to the server using node.js and HTML5.
Did you know you can enable web application tracing, performance check, request response time trace and exception tracing all free using Azure Application...
Are you wondering how to use ng-show in Angular 11? There is a way to achieve it by using [hidden]= “false”. However, if you are migrating large angularjs...
For entire azure resources even across subscriptions if you want to know about your billing, invoice, budget, alerts, recommendations then you must go to ...
You want to connect your Azure resources from your on-premise office machine or home laptop right? So how would you do that? Read this article. In order t...
Azure Advisor collects recommendations from all of the services within your subscription and display them in a single page. Example you can see recommenda...
Have you realized writing code that is not production ready is not good practice? Have you seen code which violates the DRY principle? Did you notice spec...
You can monitor performance and health of Virtual Machines and Virtual Machines scale sets, running processors and other resources dependencies with Azure...
Do you have node.js project that has specs and you want to make sure these specs run when you push your code to GitHub repo? Well you must setup CI in you...
I am happy that I cleared my Microsoft Azure Fundamental Certification (Az 900) Exam. This is the start of my Azure journey. In this article, I will expla...
Azure Security Center is the base infrastructure service to collect logs analyze them and generate tailored recommendations. Learn how can you review and ...
Do you have node.js project that you want to write specs using Jasmine? Are you wondering how to write specs and run all specs in your node.js project? Le...
This article will teach you the how to configure and implement diagnostics log for Azure resources. This article will help you to prepare for az-303: Mi...
Webbooks are basically user defined HTTP callbacks which are triggered by specific events. Whenever that trigger event occurs in the source site, the webh...
Azure Service Bus is a transport layer comprises of messaging entities. Learn what is Topology in messaging world and how N-Service bus makes life easy by...
Learn Merge Sorting algorithm in recursion function. In this article I will show you the execution of the recursion function for Merge Sorting.
Microsoft Azure Solutions Architect Expert is a role-based certification with a 1 year expiry.
Learn how to help your company to migrate its database workload to Microsoft Azure. How can you use Azure Cosmos DB to migrate your data to cloud and reta...
In order to become Azure Solution Architect Expert You must give AZ-303 and AZ-304 certification exams.
Can you explain concepts and terminology for the core Azure architecture components? Can you describe the benefits and usages of Azure subscriptions and m...
Do you love open-source? Do you want to make your PowerShell really powerful? Consider installing scoop and make your life simple! 😄 Learn how can scoop h...
Do you love open-source? Do you want to make your PowerShell really powerful? Consider installing scoop and make your life simple! 😄 Learn how can scoop h...
Do you want to understand binary search? Read this article, I have discussed binary search problems in JavaScript.
Did you know your company can take advantage of using many Azure cloud computing which will help your company to reduce its overall computing costs? Did y...
Do you want to build your first Angular App and deploy over cloud using GitHub Actions? How to deploy/publish Angular App to GitHub Pages automatically? D...
Microsoft offers 6 kinds of support plans. In this article lets quickly check them out.
While building/compiling angular or node application on Local Build Machine or Azure Pipelines or GitHub Workflows or Netflix or Heroku. The main issue we...
Microsoft offers 6 kinds of support plans. In this article lets quickly check them out.
Azure Information Protection (AIP) is a cloud-based solution that enables organizations to classify and protect documents and emails by applying labels.
Creating Azure Function in Csharp
Do you want to create your own custom GitHub Action? It’s very simple & really fun! In this article I will walk you through the steps to write, test, ...
Azure Load Balancer evenly distributes incoming network traffic load among backend resources or servers. It works at layer 4 (Transport Layer) of OSI (Ope...
Are you wondering how to publish Test Results over Azure CI Build while using Angular and JEST? In this article I will demonstrate nx monorepo publishing ...
Azure Information Protection (AIP) is a cloud-based solution that enables organizations to classify and protect documents and emails by applying labels.
In order to become Azure Developer Associate you must pass AZ-204 exam. If you want to become Cloud Solution Architect then consider giving Microsoft AZ-2...
Can you describe basic concepts of cloud computing? Is Azure right solution for your business needs? How can you create your Azure subscription today? I w...
Learn some important built-in very helpful methods in Powershell. It could be a quick note for you so don’t forget to bookmark this article! 🥇
Learn everything you should know about Azure Services and their concepts as a beginner.
Have you tried to host NServiceBus within Azure Functions? In this article I will teach you how can you host your first NServiceBus project within Azure F...
When I was learning Azure Infrastructure, I had big question in my mind what is subnet and why do I need Subnet in my network? If you share my question th...
When I was learning Azure Infrastructure, I had big question in my mind what is subnet and why do I need Subnet in my network? If you share my question th...
Do you prefer LINQ queries? I do because they provide a single consistent programming model across how they work with objects in application code and how ...
Are you wondering how your function app authenticate & authorize to read or write to Azure SQL table? Do you think how your web application will get p...
Are you wondering how your function app authenticate & authorize to read or write to Azure SQL table? Do you think how your web application will get p...
Do you want to create dotnet csharp console app and write CRUD ( Create, Read, Update and Delete ) operations over Azure Cosmos DB noSQL data? Read this a...
Did you know you can create and deploy Azure resources using JSON template? Did you also know that you can enforce business compliances on your resources?...
Do you want to make your PowerShell prompt colorful? Please read this article to make your PowerShell Terminal colorful and Git supported. I will use oh-m...
Did you know you can create and deploy Azure resources using JSON template? Did you also know that you can enforce business compliances on your resources?...
Do you want to learn Azure and afraid of being charged your credit card or getting big bills? Learn this article where I will explain how you can get free...
Are you wondering how to enforce business compliance to the deployed resources over Azure? Did you know you can write configuration file to deploy resourc...
Do you want to create Cosmos DB & Collection from DotNet Core Project? Read this article to create your first .net core project. And write csharp code...
Do you want to refresh AZ 304 Microsoft Azure Architect Design related random questions? This article will give you great random flashcards to remember Az...
Do you want to create your new Cosmos DB account and first database and collections right from Visual Studio Code? Read this article to learn hands on cod...
Did you know you can write a script and run from your machine to create and destroy multiple cloud infrastructures? Well yes I am not joking this is possi...
Are you using repository pattern? And want to commit multiple repository operations as a single logical transaction in Azure Cosmos DB? Read this article ...
.Net running on-process till .Net Core 3.1 & .Net isolated workers are coming on .Net 6 onwards & you can deploy Azure Function Apps in production...
Are you beginner on Azure Functions and want to learn the basics of Azure Functions? Did you know you can create Azure Functions and publish to Azure usin...
Do You want to start IT Business and you don’t have equipments? Don’t worry Azure is the solution for your business. By using Azure Compute Resources you ...
Did you know how can you protect your business against software or hardware disaster within Azure data-center? Did you also know how can you protect your ...
Are you beginner on Azure Cosmos DB and want to know what exactly is Cosmos DB? Then read this article. Azure Cosmos DB is a fully managed NoSQL database ...
Do you know in Azure Data Center you can protect your server against regular server software maintenance outages? You can also protect your VMs on Azure a...
Convert Angular service to a Message Handler. Do you want to organize your Angular code base as Service Oriented Architecture (SOA) way. And you want to c...
I have WordPress or Blogger blog and I decided to move away from WordPress and switch to Jekyll. I loved the way Jekyll is working. You can deploy Jekyll ...
Are you non-computer background student? I am a Electronics Engineering student and have been in software company and worked more than 16 years from junio...
When I started learning coding for a coding-interview for Facebook, Amazon or Google. I faced problems when I saw programmers were using terminologies lik...
Did you know how your servers are placed in Azure Data-Center? Do you understand how Azure Data Center protects your servers against software or hardware ...
Are you preparing for cloud solution architect interview then you must aware of soft skill questions. In this article I will give you questions that you m...
Learn how can you can create & host your own new Blog site for FREE. With high performance and SEO enabled using Jekyll and host them in GitHub Pages....
Are you willing to become cloud solution architect? I am going to add a few important technical questions that you must know for your next cloud solution ...
Did you know Azure DevOps Services and Azure DevOps Server are different entities? I have learned lessons while working on Azure DevOps Server 2020 on-pre...
Learn how Storage Spaces Direct provides you a Data fault tolerance at verity of levels. You don’t loose data at any stage. You get Data resiliency out of...
Do you want to show Angular Code Coverage Report in Azure CI Pipeline then read this article and follow the steps. IstanbulReporter in Karma.conf.js Go...
If you are working on nx monorepo workspace and if you have notice below error and want to fix it then read this article. “Error: A project without tags c...
Understanding Azure architecture gives you power to learn lots of higher level concepts on Azure like Virtual Machine scale sets etc. Therefore, in this a...
Do you want to schedule your Jekyll blog post to be published on GitHub Pages on future date time? Then read this article. Introduction Jekyll static s...
Do you want to restore and publish your scoped and public npm packages from Azure CI Pipeline? Do you want to Configure CI/CD for Node application with Az...
Artifacts caching does not work on-premise Azure DevOps Server 2020. The Azure DevOps documentation on Cache Action is not updated and that is misleading....
Do you want to know how to tag your git branch while building your source code when someone commits or merge to MASTER/MAIN branch? Then please read this ...
Are you wondering how to create an .npmrc file and put an authentication token from azure devOps for your team member’s development boxes? Do you have mul...
Are you using windows machine for local development? Do you have Azure DevOp’s server git repo and want to connect from local box? Then read this article....
Do you want to follow Conventional Commits and want to enforce a rule such that your team also follows it? In this article, You will learn how to enforce ...
Are you worried that new angular 10 project is not running in “IE11” even though you enable the given polyfills by angular team? Then please read this art...
Do you want to organize your CSS files in your angular app? Do you want to find out the strategy to segregate the CSS based on cross browsers and operatin...
If you are working on Nx Monorepo workspace and have many angular projects. And if you are using Azure CI/CD Pipeline then you might aware that there is no i...
If you have a blogging site using Jekyll and you want to publish your blogs to your Dev.To account? Then read this article. Jekyll Project I have my Jekyll...
So you want to learn how you will integrate CkEditor v5 in Nx Monorepo. Do you also want to learn how to create custom plugin inside CkEditor v5? Then I w...
If you want to run node.js script from azure-pipelines.yml and get the value returned from node.js script and use it in your CI next task. Then read this ...
Publish Test Results task publishes test results to Azure CI Pipelines. Step 1: Publish Unit Test Summary Report Step 1 - To generate Test Report I’m using...
Did you have requirement to update your Angular CI build number as your new Package.json version number and Branch name? Well this is a good practice to d...
Publish Code Coverage task Publishes Cobertura or JaCoCo code coverage results from your build in azure CI Pipeline. Azure DevOps provides us with the a...
Do you want to create environment level variable for your Azure Build CI Pipeline and access them in your azure pipeline task? Example: If you are using n...
Do you want to debug your NRWL/NX monorepo specs in visual studio code or right in chrome? Then this article is for you. I am going to use JEST test runne...
In my previous article “Imposing Constraints on Dependency Graph” you did learn how to isolate all projects of a folder (service A) from all of the projec...
Do you want to publish your nx monorepo app to npmjs.org? In this article, I will explain how can u publish your app to npmjs.org. Introduction In my m...
Are you using NRWL/NX monorepo in your company? and you are worried how to configure dependencies so that you can better control your projects? I use nx d...
In this article, I will explain how to know which applications or libraries are changed in your nx monorepo workspace. First time building Nx Monorepo ...
Do you want to create a new application on my nx monorepo work-space? Also do want to make sure that you should be able to build and test your application...
Do you want to create one variable in task-1 and read the value of that variable in task-2 in your azure ci pipeline? If your answer is yes then read this ar...
Protecting Master Branch from Bad Pull Requests is big challenge now a days while working in a team. You are working on git with distributed architecture. Wh...
Subscribe to email alerts to get notified for your build CI/CD in azure pipeline. It is good idea to setup subscription to get email to a group email id...
All are hosted CI/CD server supporting the build running in the build machines and deployment to target machines. Travis CI A hosted continuous int...
If you are following agile then continuous integration is must. I have setup CI/CD in Azure DevOps and I personally found my Angular build is taking lot of t...
If you want to create Build definition for Angular project in Azure DevOps, then this article is for you. Login to Dev Azure and go to the pipelines and foll...
Yaml files are used in Azure Pipelines for build and release definition. Yaml files are also used in GitHub build and release. Yaml is designed to be clean a...
In this video tutorial 0010-4 JWT authentication for distrubuted system we will learn what makes JWT authentication world’s most popular authentication type....
As we already discussed rest of the authentication types in our previous video tutorials, JWT based authentication is best among all. It is world famous and ...
In this video tutorial Cookie Based Authentication Advantage And Disadvantage | 0010-02 we will discuss about cookie based authentication. In this type of au...
Authentication is vital to most of the applications and the way it is achieved has evolved substantially in recent years. Basically there are three types of ...
About the Class Learn how to build an e-commerce online shopping responsive web application from scratch using Angular 8+, express & MongoDb comple...
Whenever somebody asks developer about difference between server side & client side coding, generally answer comes as “Anything angular or HTML code or a...
What is User Story A User Story is a note that captures what a user does or needs to do as part of her work. Each User Story consists of a short descripti...
In this video session Given When Then | Angular | BDD, we will teach you how to write unit tests in more readable fashion. Like Given When Then Style using J...
In our previous video session Add Item To Cart | Test Driven | RxJS | Demo we have already discussed Add item use case in our shopping cart project. Next in ...
In our previous demo session Creating Store Using RxJS | Angular | Demo we have written base code for our Cart Store. Now we will add methods to it, based on...
In this video session Creating Store Using RxJS | Angular | Demo we will create our Cart store and it is nothing but just a wrapper on top of state, so it be...
Till now in previous demo session Responsive Products Page | e-Commerce | Angular Material | 2 we have done loading of products with spinner, applied sorting...
In our previous demo session Responsive Products Page | e-Commerce | Angular Material | 1 we discussed how to use mat-table rather mat-cards or mat-grids in ...
In our previous demo session Pagination And Filter e-Commerce Angular App | mat-table we have covered filtering and pagination functionality in our ecommerce...
As we already fixed design and responsiveness of Login and Register pages of our ecommerce app in previous demo session Creating Responsive Login And Registe...
In our previous demo session Responsive Toolbar Online ecommerce Store Part 2 we have learnt how to create responsive toolbar with proper design. Next in thi...
In continuity to our previous demo session Responsive Toolbar Online eCommerce Store Part 1 where we made required changes to our ecommerce store to make its...
After learning error handling in our previous demo session Handling Server Side HTTP Error | 0009-27, next we will focus on creating responsive toolbar in ou...
🔥 Master the real, in-demand tech skills from home with Full Stack Master 100% online learning platform. Come out of this disaster with higher-paying,...
As we discussed in our previous video session Designing Shopping Page Using Angular Material Grid And Card | 0009-26, our web app is now growing as we are ad...
As we already discussed in our previous demo session like with growing maturity our code becomes complex and difficult to debug. Then we come up with this de...
Gradually, as our code base will grow it will become complex and we will face difficulties in debugging our code. In this session Debugging Server Side Code ...
Save the below code in bat file and execute it. It will install all the important VS Code Extensions that you need to do Angular / React or any Front End De...
While writing test in jasmine you will encounter a situation where you want to create a mock object & also you want to spy it's property. Jasmine cre...
In this video session User Login In Angular With MongoDB | Demo | 0009-23 we will login into our product Mart app through MongoDB database and we will see ho...
[iframe src="https://mailchi.mp/f98949daab5f/build-online-e-commerce-application-meanjs-full-stack-the-complete-course" width="100%" height="3500px"]
Fullstack Development Training
In this video session Saving User To MongoDB | Mongoose | Demo | 0009-22 we will explain how to save user data in mongo db and how to validate user at server...
[advanced_iframe securitykey=”” src=”https://gumroad.com/fullstackmaster/p/up-coming-full-stack-master-courses” id=”” name=”” width=”100%” height=”1500px” m...
Now in this demo session Installing And Configuring Mongodb & Mongoose | Demo | 0009-21 we will see how to install MongoDB in our machine and how to use ...
Introduction Now a days event based architecture is very popular. Writing JavaScript web application from scratch using event based architecture is a grea...
In our previous demos session we have created our server and restful API and tested API with postman also. Next we will try to integrate this Restful API in ...
In this demo session Creating Endpoint For Authentication | Express | Demo | 0009-19 we will create a restful API and will host it in Node.js using express. ...
Let’s begin this demo session 0009-18- Demo: Adding Registration and Logout feature with change in some look and feel of our user registration page, by impor...
In this demo session Creating Registration Component | Angular | Demo | 0009-17 we will first create registration component which will allow us to save user ...
In this demo session Adding Log In Component | Angular | Demo| 0009-16 we will learn to implement Login functionality in our app. With this functionality, us...
In our previous demo sessions we successfully created our Product Mart app. Now we are ready to deploy our code to so called production environment. For this...
Nowadays, we build large enterprise applications with Angular. But how to best structure such projects to ensure long-term maintainability and re-usability?...
In this demo session Integrating Toolbar | Angular CLI | Demo | 0009-13 we will see how to integrate toolbar in our angular app. In order to put toolbar in o...
This demo session Applying Card Component | Angular Material | Demo | 0009-12 talks about integrating card components from angular material so that we can p...
In this demo session Creating Product Service | Angular Service | Demo | 0009-11 we will see how to show products from JSON file in our angular project. Each...
In continuity of our demo session Creating Products Module | Lazy loaded module | Angular | 0009-09 we will see how to create Products page for our app keepi...
Let’s begin this demo session Creating Products Module | Lazy loaded module | Angular | 0009-09 by creating a home component. Command used to generate home c...
As we discussed in our last demo session Installing Angular Material Using Angular CLI | Tutorial | 0009-07 we are missing out component module installation ...
In order to install required angular material, angular team has provided six steps to follow in angular material home page. All of them are listed when we cl...
As you begin learning of coding basics, one important thing which makes your learning process easier and practical is availability of code. Most of the onlin...
So far in our angular project development from scratch we have covered two things: Environmental setup Creation of project using angular CLI An important q...
We saw in our previous session Creating Angular App using Angular CLI | 0009-03 how to do environmental set up and installation for our first angular project...
Let’s begin our Angular app development project from scratch. This article explains each step very minutely, so that you do not feel lost anywhere. It also s...
MEAN is an acronym for MongoDB, ExpressJS, AngularJS and Node.js. From client to server to database, MEAN is full stack JavaScript framework, ideal for build...
There are certain steps that we need to understand thoroughly to begin any angular project from scratch. In our previous video tutorial we already explained ...
When we talk about angular app development, most of the people get confused about its build & deployment activities. Our video tutorial Angular app Devel...
The Prototype Pattern creates new objects, but rather than creating non-initialized objects it returns objects that are initialized with values it copied fro...
In our previous video session JavaScript Concepts- Module Pattern | 0004-11 we have learnt about basics of Module Pattern. Here in this video tutorial JavaSc...
The Module Pattern is one of the most common design patterns used in JavaScript. It is easy to use and creates encapsulation of our code. Before we deep dive...
In our previous article JavaScript Concepts: What Is this Keyword | 0004-08 We read about ‘This’ concept of JavaScript which refers to calling context of the...
‘This’ keyword is widely used in almost all programming languages. Like in some programming languages This variable points to instance of an object or class....
Hoisting is another important JavaScript concept. It defines that in JS every variable gets declared at the beginning of the function. It literally means as ...
Closure is another JavaScript concept which comes in line with Scope concept. It basically comes into picture when we have nested functions. Whenever we have...
Though the concept of scope is not that easy to understand for beginners, yet we have tried to explain it in easiest way in our video tutorial JavaScript Con...
If you are planning to accelerate your career as JavaScript Professional, you must know some basic JavaScript concepts. Here in our video tutorials we have e...
In our eighth angular coding session Angular Coding Session Learn Dependency Injection | Practical | 8/8, we will see how to dynamically inject the console o...
In our sixth angular coding session Angular Coding Session Learn Dependency Injection | Practical | 6/8, we will see how to configure logger based on environ...
In our fifth angular coding session Angular Coding Session Learn Dependency Injection | Practical | 5/8 we will see how to create mini-logger by using existi...
In our fourth angular coding session Angular Coding Session Learn Dependency Injection | Practical | 4/8, we will see how to Inject Base URL from module in o...
In our third angular coding session Angular Coding Session Learn Dependency Injection | Practical | 3/8 we will see how to use http logger as a service in ou...
In our second angular coding session Angular Coding Session Learn Dependency Injection | Practical | 2/8, we will see how to use console logger as a service ...
As we know about Dependency Injection in detail like what is DI, where to use it and what is its significance? So in order to understand Dependency Injection...
Memory Issues Trouble shooting memory issues in web application is very important and it needs careful understanding of memory analysis. There are various...
A provider is an instruction to the DI system on how to obtain a value for a dependency. It is the provider that determines which instance or value should be...
As we know UseExisting provider configures the Injector to return a value of another UseExisting token. Through this provider, we can use already existing in...
Multi: true means that one provider token provides an array of elements. Using multi: true we tell Angular that the provider is a multi provider. This is use...
UseFactory provider configures the Injector to return a value by invoking a UseFactory function. It is basically a function which follows factory design patt...
UseValue provider configures the Injector to return a value for a token. It comes in that category of providers where we do not have unique thing to identify...
UseExisting provider configures the Injector to return a value of another UseExisting token. Through this provider, we can use already existing instance or o...
Class Provider configures the Injector to return an instance of useClass for a token. It is similar to type provider but it has different way of providing co...
A provider is an instruction to the DI system on how to obtain a value for a dependency. Most of the time, these dependencies are services that you create an...
There are 2 types of architectures one is Pull Based the second one is Push Based. I will explain you how can we leverage RxJS BehaviorS...
What are RxJS subjects and the benefits of using them. How to understand RxJS subjects such that you can apply it in your day to day coding at your own p...
Heroku PaaS best Cloud Platform Heroku is a cloud platform that lets you to build, deliver, monitor and scale application. Heroku is Platform as Service (Paa...
Angular 8.0.0 is here! Is there any breaking changes in Angular 8? No, Angular 8 is released now! As Angular team had promised they have not introduced break...
Introduction Welcome to step by step hands-on guide to setup webpack in your upcoming typescript project. Please follow the steps and you should be able t...
Unit Testing RxJS with Marble Diagrams Welcome to Unit Testing RxJS with Marble Diagrams course excercise material portal. Please watch Uni...
Scope of Dependency in Angular is very important concept to understand for a full stack developer. This is primarily asked question by interviewer in many di...
As we know, one must configure an injector with a provider, or it won't know how to create the dependency. The most obvious way for an injector to create an ...
A Dependency Provider configures an Injector with a DI Token, which that injector uses to provide the concrete, runtime version of a dependency value. The in...
We cannot simply ignore the shortcomings like Interface, Array (bunch of objects) cannot be used as DI Token in angular. There can be possibility where we ne...
No, we cannot do dependency injection through Interface in Typescript Angular; it can be done in C# or Java. This is very important concept need to know for ...
When we think of learning Dependency Injection in Angular, couple of questions arises like How this DI concept works in Angular? What are all the important ...
React: React is a JavaScript library for building UI components for web applications, maintained by Facebook. React Native, another popular outcome from Face...
Due to its component based architecture, angular has capability to protect our code for future. It is basically making our code future ready as each componen...
One of the main architectural principles in Angular is that an application should be composed of well encapsulated, loosely coupled components. In this sessi...
In 0008-7- angular: Hierarchical Dependency Injection video session, you will see how Angular hierarchical dependency injection system works. You will discov...
Most of the applications connect to multiple environments during their lifecycle. Environment which your application needs to connect can differ depending on...
Angular has a unique feature that makes it more popular and provides an upper hand as compare to other app building platforms like vue JS, React JS i.e. its ...
Dependency Injection Container or Injector is basically a static or global thing which is being used throughout the app to inject dependencies or objects. It...
Basically there are three types of dependency injection, Depending on the context we can choose any type which is being supported by that framework. Three ty...
Wikipedia Definition: Dependency injection is a technique whereby one object (or static method) supplies the dependencies of another object. A dependency is ...
Are you preparing for Angular interview? Not sure from where to start? Well we do have answers to all your angular related queries. We will help you to list ...
Along with choosing right template, best resume format, putting educational qualifications etc, the most important component required in an interview-winning...
Did you know you can create your own publish-subscribe library for your RxJS project? By using BehaviorSubject and filter operator it is possible to create ...
Did you know you can use RxJS simple operators and do html form validation re-actively? Well I learn RxJS operators by implementing them in real world proje...
I love to create automatic API Documentation of my project. Regardless I work on Angular, React or VueJS as far as it uses Typescript. Did you know you coul...
You might be aware of EADDRINUSE node error in node.js application. Where it says address is in use. This is very annoying. It happenes if some of the port...
I love Typescript the way it helps development speed and accuracy. I wanted to work with Typescript, Webpack and Express.JS finally came up with a project w...
Model in Domain Driven Design is a system of abstraction that eliminates things which are not required. Domain Model allows us to think about a particular do...
How to Inject Base Assets path URL dependency to webpack CSS bundle? In your JavaScript project build by webpack, if you have requirement where at the build ...
Dependency Injection In Software Engineering Dependency Injection is a technique where one object injects or passes the dependency object to other object at ...
Decorator is a concept in Typescript that can be used to annotate a class or it's members. Decorator also enables meta programming where one can collect as ...
Loading... In this article we will see how can you create your own typescript library that you can easily consume in your another typescript project. ...
RxJS Marble Diagrams are made to visualize the values emitted from the RxJS Observable over timeline.</p> Hi in this article I will explain why we need...
In this article we are going to talk about. What goals are ? How to set Goals ? What makes really good goal ? Organize your life goal Sort out your lif...
What is Scope in JavaScript Imagine Scope as a boundary within that things can be isolated. Like in your colony there are certain areas which has stuffs that...
When you create your own Typescript library then you need a barrel file where you put all of your files that you want to expose to the outside world kind of...
Eric Even wrote Domain Driven Design (DDD) book. Eric says DDD is the Philosophy of software design that helps projects dealing with complex problem. I ...
Why JavaScript I believe JavaScript is very popular language nowadays. I love JavaScript because of many reasons. Now various powerful client side framework...
How to add your own logo on README.md file Here is a simple way to create your own logo for your npm package. I hope you will enjoy this. Where to go and get...
What is GhPages Do you want to save time to create post or article while writing software code ? Or do you want to see your angular app live running in the i...
This blog post supports the sample code for the “Unit Testing RxJS with Marble Diagrams” course on Pluralsight, identifying common issues along with their so...
Hi everyone, I am very excited to announce that I became an author in Pluralsight.com and my first course on Unit Testing with RxJS Marble Diagram is going t...
Hi everyone, I started my FullstackMaster YouTube channel where I want to put some technical learning stuffs. I started putting RxJS videos over there. I hop...
Cloud itself is complex so why are customers bothering about multi-cloud at all? Why not just take google cloud and deploy all of your workload and be hap...
I recently wrote one article on JavaScript Module pattern in Code project. Please visit this website and suggest me your thoughts on it... Javascript Module ...
Today, I learned about one Excel Sheet Formula "VLOOKUP". It is very useful formula that gives us the power to search a value in a particular column. ...
I came through an open source JavaScript named as “Knockout.js”. After learning this javascript functionality and features. I found it very powerful, wh...
I took session on jQuery. It was nice experience to talk in front of my colleagues. First time I took session where some of my colleagues joined on phone als...
Suppose you are searching for a product in a shopping website and you got a big set of results. It normally comes in a grid view with a long scroll bar. Some...
My Friend was looking for one error that he was continuously getting when he was trying to setup my old version 1.0 .net code. The error message was: Th...
From last 4 days, I have been struggling on how I should load the UserControl dynamically in my default page. I know in today’s world where .Net 4.0 came up...
In order to make the application more loosely coupled we should use interfaces. In Dependency injection pattern there exist a class called as asse...
Almost 3 years ago Scottgu announced that Microsoft would begin offering product support for jQuery. Now Microsoft is playing a great role on contri...
I was trying to make my own menu widget using jQuery and I came with this below Widget. [sourcecode language="javascript"] //Menu Widget created by Rup...
In any jQuery Plugin there JavaScript local alias pattern is being used as a best practice. They have localized the global jQuery object as an alias $. ...
At the outset, I used to write programs that just work because, I had to complete and deliver the project on time.</p> I remember, when was a...
Recently, I received one question how to send the xml data from one page to another page without using any state management or caching technique of Asp...
Hi all,</p> I recently installed Internet Explorer 8 in my laptop and wondering many new features about the IE8. I was enjoying the good and...
I just read the great article Introducing "Razor" – a new view engine for ASP.NET by Scottgu. I found Razor more comfortable than the other view engines. It'...
Plethora of times it is required to show complex tool tip. Complex, I mean the tool tip that can contain images, links , text decoration etc...To show the cu...
Hi I just came across a greate website http://bililite.com/blog/understanding-jquery-ui-widgets-a-tutorial/ There I learned how to create custom jQuery widge...
There is a great article written by Douglas Crockford. I recommend everybody to read this article. By using Prototypal inheritance technique, we can create t...